WordPress Security Alert – WP Super cache

Upgrade immediately
Security firm Sucuri revealed on their blog this week that they had uncovered a persistent cross-site scripting vulnerability in the popular WordPress plugin WP Super Cache. The effects of this vulnerability can be severe as an attacker can potentially insert malicious code into WordPress pages without your knowledge. Anyone who has experienced this type of attack due to a plugin security flaw knows how difficult and time consuming remediation can be.
 Cypress North
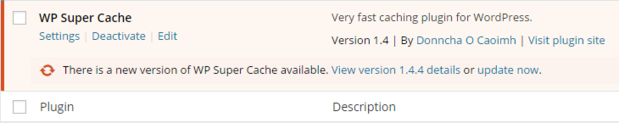
Cypress NorthWP Super Cache is deployed across all of the WordPress sites we host in our data center, and for good reason. The excellent plugin dramatically boosts the performance of WordPress sites while simultaneously reducing load on the web servers. The code for this plugin is mature and stable, rarely requiring updates. That’s part of the reason why it’s trusted by over 7 million websites. It’s popularity makes this security flaw a big concern for site owners.
 Cypress North
Cypress NorthThe update process is quick and easy so you should take the time to log in and click the update now link as soon as you’re able. If you’re fortunate enough to maintain your sites under a multi-site install you’ll be able to take care of this issue in one shot. Otherwise, like us, you’re stuck logging into each installation and manually updating each site like we spent all yesterday doing.
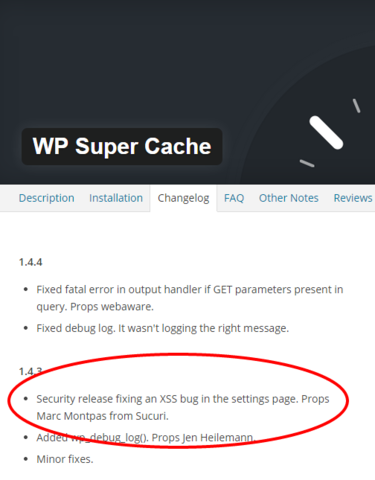
According to the blog post by Marc-Alexandre Montpas:
Using this vulnerability, an attacker using a carefully crafted query could insert malicious scripts to the plugin’s cached file listing page. As this page requires a valid nonce in order to be displayed, a successful exploitation would require the site’s administrator to have a look at that particular section, manually.
The nonce requirement lowers the odds of the backdoor taking effect since the cached page gets purged periodically, but still, better safe than sorry. The scale of the vulnerable sites makes exploitation an inevitable event. Do your part to protect the web and get updating.
